![]() A large travel management firm last week had to pay hackers over $6 million in a ransomware attack which encrypted its sensitive corporate files – and the Office of the Australian Information Commissioner has warned of growing risks to Australian businesses from such attacks, which have increased by more than 150% in the first half of this year.
A large travel management firm last week had to pay hackers over $6 million in a ransomware attack which encrypted its sensitive corporate files – and the Office of the Australian Information Commissioner has warned of growing risks to Australian businesses from such attacks, which have increased by more than 150% in the first half of this year.
US travel management firm CWT paid US$4.5 million (about A$6.3 million) in the digital currency bitcoin last week to hackers who stole sensitive corporate files, Reuters reported.
Reuters said it had seen a record of the ransom negotiations – which, bizarrely, remained publicly accessible and visible in an online chat group. The news agency published texts between the hackers and a negotiator representing CWT.
The attackers used a strain of ransomware called Ragnar Locker, which makes computer files useless by encrypting them, until the victim pays to regain access. There’s no guarantee the hackers will keep their side of the bargain.
Reuters said CWT, which posted revenues of US$1.5 billion last year, confirmed the attack but gave no details, other than to say there was “no indication that personally identifiable information/customer and traveller information has been compromised”.
Investigations continue.
Similar attacks are thought to cost billions of dollars each year. Security experts say each ransom payment encourages cyber-criminals to mount further attacks.
Another travel-related operator, the international currency exchange company Travelex, was attacked successfully by ransomware hackers on New Year’s Eve last year.
Just a week ago, cybercriminals temporarily crippled the navigation and fitness giant Garmin, with a ransomware attack that took down services across the company.
The Office of the Australian Information Commissioner (OAIC), a federal government agency, defines ransomware as a strain of malicious software which encrypts the data stored on the affected system, rendering the data either unusable or inaccessible.
Below: Cyber incident breakdown. All sectors. Source: Office of the Australian Information Commissioner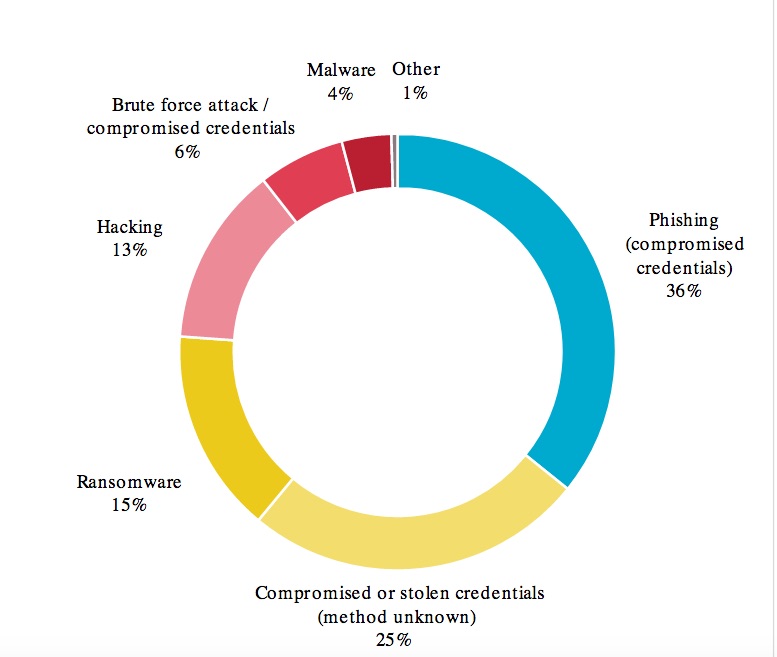
“The malicious actor behind the attack then demands a sum of money be paid for the decryption key. The decryption key may or may not be provided after the ransom is paid.”
OIAC has warned that from January to June 2020, the number of data breach notifications attributed to ransomware attacks increased by more than 150% compared to the previous six months, increasing from 13 to 33.
OIAC warns: “Ransomware can be installed on a system through a malicious email attachment, a fraudulent software download or by visiting a malicious webpage. Ransomware attackers can also gain access to a system through unsecured public-facing servers or a remote port.”
OAIC concedes that the leap in ransomware notifications it has received may be “the result of entities undertaking more rigorous assessments of ransomware incidents on their networks, resulting in more instances where entities confirm that personal information had been either accessed or copied by the attacker.
“However, media reporting during the reporting period has highlighted an increase in ransomware attacks that resulted in the copying or exfiltration of data as well as the encryption of the data on the target network. Many of these attacks appear to be linked to a specific ransomware variant.”
OIAC continues: “If data exfiltration, in addition to encryption, becomes the default function of ransomware attacks, this will have significant implications for how entities respond to ransomware attacks. Previously, entities responding to ransomware attacks would look for evidence of access to, or the export of, data before suspecting that an eligible data breach had occurred.
“Now, given growing evidence that data exfiltration tends to occur when certain ransomware variants are deployed, entities may have grounds to suspect that a ransomware attack constituted an eligible data breach at the time they become aware of the attack.
“Ransomware attacks are inherently difficult to assess and investigate because the target entity can no longer access its own network. It can be difficult, time consuming and expensive for an entity to investigate the extent of malicious actor access to its data. The entity will often have to rebuild or recreate its network to understand the extent of the compromise.
“It is critical that entities who collect and retain personal information – including the information of clients, customers, business partners, employees and contractors – fully understand how and where this information is stored on their network. They should also consider network segmentation, additional access controls and encryption to reduce the risk of personal or commercial information being exposed by a ransomware attack.
“There is increasing public awareness of the threat of ransomware attacks to Australian business, and growing evidence that these attacks often result in the exfiltration and release of information by the attacker. Entities are expected to be aware of their obligations under the NDB scheme and under APP 11.”
Written by Peter Needham
















